Identity and Access Management (IAM): A Cornerstone of Cybersecurity
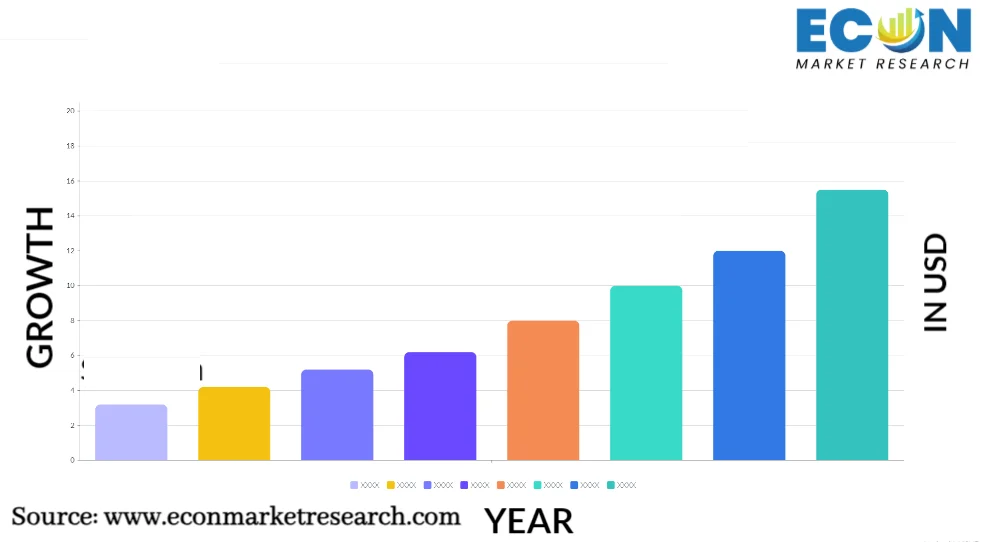
Identity and Access Management (IAM) is an essential component of cybersecurity that focuses on ensuring the right individuals have appropriate access to resources within an organization. In a digital-first world, where data breaches and cyber-attacks are frequent, IAM serves as a gatekeeper, controlling and managing user identities and permissions to secure sensitive information and applications. From setting up single sign-on (SSO) to multi-factor authentication (MFA) and role-based access control, IAM offers a comprehensive framework to verify user identities, limit access, and prevent unauthorized data exposure. Effective IAM enhances security, ensures regulatory compliance, and enables seamless user experience across digital platforms.
More Info : https://www.econmarketresearch.com/industry-report/identity-and-access-management-market/
The Key Components of IAM: Authentication, Authorization, and Accountability
IAM encompasses several critical functions, each aimed at different aspects of user and access control: authentication, authorization, and accountability. Authentication verifies the identity of a user, often through passwords, biometrics, or tokens. Authorization, on the other hand, defines what authenticated users can access and control, enforcing permissions according to job roles, responsibilities, or security policies. Finally, accountability involves tracking user activities and logging access details for future audits, supporting compliance and monitoring for potential threats. Together, these components ensure that only legitimate users can access specific systems and that their actions are tracked and controlled.
Identity Governance and Compliance in IAM
Identity governance is a critical aspect of IAM that ensures organizations remain compliant with regulations by managing and overseeing user access rights and monitoring for potential risks. IAM helps organizations establish policies for identity lifecycle management, access reviews, and segregation of duties, which are necessary to meet regulatory requirements such as GDPR, HIPAA, and SOX. Regular audits and automated access reviews within IAM systems help maintain compliance by ensuring that users have appropriate and timely access. This governance framework not only supports regulatory adherence but also enhances data security by reducing the risk of privilege misuse or unauthorized access.
The Importance of Privileged Access Management (PAM)
Privileged Access Management (PAM) is a specialized IAM area that focuses on securing and controlling access for users with elevated permissions, such as IT administrators and executives. Privileged accounts have greater access to critical systems, making them prime targets for cyber-attacks. PAM solutions limit and monitor privileged access, employing methods like just-in-time access, where permissions are granted only when needed and removed once the task is completed. By closely managing and auditing privileged accounts, PAM prevents abuse and mitigates the damage from potential insider threats or compromised accounts, ensuring higher levels of security for sensitive assets.
Emerging Technologies in IAM: AI and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are transforming IAM by enabling smarter, more adaptive security measures. Through AI, IAM systems can analyze large datasets to detect unusual user behaviors or anomalies, such as access attempts from unexpected locations or devices. This behavior-based analysis allows for rapid, automated responses to potential security threats. ML algorithms also improve the accuracy of access control by learning patterns over time, making IAM systems more resilient and efficient. As cyber threats become increasingly complex, AI-driven IAM will be crucial in providing proactive and adaptive security measures.
IAM in the Era of Cloud and Remote Work
The rise of cloud computing and remote work has significantly impacted IAM, as employees now need secure access to systems from virtually anywhere. Cloud-based IAM solutions enable organizations to manage user identities across on-premises and cloud environments seamlessly. Cloud IAM provides scalability and flexibility, allowing companies to add or remove users easily as business needs change. It also facilitates integration with other cloud applications, ensuring consistent security policies across platforms. With remote work becoming the norm, IAM solutions must also account for new security challenges, offering tools like remote MFA and secure, role-based access to protect data in decentralized work settings.
Future Trends in Identity and Access Management
The future of IAM is moving towards more adaptive, decentralized, and user-centric approaches. Decentralized identity, powered by blockchain, is an emerging trend where users control their own identity credentials, reducing reliance on centralized authentication systems. Similarly, the integration of biometric authentication methods, such as facial and voice recognition, will continue to grow, providing more secure and seamless user experiences. With advancements in AI, future IAM solutions will likely become more proactive, using predictive analytics to anticipate access needs and detect threats in real-time. As organizations adopt digital transformation strategies, IAM will evolve to address new security challenges while enhancing usability, flexibility, and resilience.
Contact Info
Phone Number: +1 812 506 4440
Email : sales@econmarketresearch.com
- Questions and Answers
- Opinion
- Story/Motivational/Inspiring
- Technology
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film/Movie
- Fitness
- Food
- Oyunlar
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness
- News
- Culture
- War machines and policy

